Unleashing the power of the e-Residency program, and the DigiDoc software

When the media talks about the e-Residency program of Estonia, the aspect that gets all the attention is how it allows location independent entrepreneurs to launch and run an online business without ever visiting Estonia. However, the true power of the digital nation lies in its foundations, namely, in your digital identity, backed by a strong cryptographic background, that you can leverage thanks to tools such as DigiDoc.
In this article, I talk about the possibilities of your e-Residency identity. Things you probably didn’t know you can do thanks to the cryptographic chip contained in your ID card. Don’t worry, I know the word “cryptography” is scary. I will keep this post strictly easy to read and understand by everyone, even if you are a non-IT savvy person.
The DigiDoc Software
Estonia offers a series of tools to unleash the power of the e-Residency card to sign documents, verify signatures from other people, and encrypt files. The best-known is the DigiDoc software, currently on its 4th version: DigiDoc4.
This application is also a good way of testing that your card works, and getting used to some of the cryptographic concepts behind the e-Residency program. It can be downloaded from the same page where you got the plugins for your browser. It’s also available on Apple’s App Store and Google’s Play Store.
If you install it on your device, make sure to get the official RIA version (the developer is Riigi Infosüsteemi Amet). You will also need an adapter to make the USB card reader work with the USB-C or lighting port of your smartphone or tablet.
The interface of DigiDoc is quite simple. It only has three main options: “Signature”, “Crypto”, and “My ID”. The first one will allow you to sign documents. As you probably know, the e-Residency program allows you to sign a document with the same legal validity as your handwritten signature.
In fact, the digital signature is a lot more secure. While it may be relatively easy to forge your handwritten signature, it’s very unlikely that someone can forge your digital signature.
The second one allows you to encrypt documents so only a specific recipient will be able to open them. This is especially interesting for sharing private agreements or information securely between parties.
Cryptography 101 For Dummies e-Residents
So how does that work? Without going into technical details of how asymmetric cryptography works, let me describe you what’s going on inside your ID card.
The cryptographic chip in your e-Residency card has two “keys”. One of them is a public key, and another one is a private key. The first one can be shared openly with the rest of the world. It identifies you digitally in front of other people, and allows them to send you private messages or documents, or verify that a document is signed digitally by you.
The private key should be kept away form prying eyes, and gives you control over your digital identity. It allows you to sign documents digitally or access messages that only you are supposed to see.
The beauty of this system is how these keys are related. Everything that is done with one of them can be undone or verified only by the other one. The system is secure.
A document encrypted for specific recipients can only be opened by them (or someone in control of their private keys and PINs). Nobody else will be able to access that information. Neither an evil hacker nor the government of Estonia will be able to understand it. Let’s see how that applies to the processes we mentioned earlier: signatures and encryption.

Message In A (Signed) Bottle
Signing a message is a mathematical operation performed on the 0s and 1s of the document (yes, every document in your disk is just a long sequence of 0s and 1s). And it’s a very complex one. To sign a document, you use your private key and the document data as input. The signature algorithm does its job with that data and outputs another sequence of 0s and 1s. That is the signature, usually stored as a file.
Then, thanks to the “magic” of asymmetric cryptography, using the public key, we can reverse this process and verify the signature. The inverse operation takes the signature obtained in the previous step, and the public key of the person who signed the document.
The output is a YES or NO answer to the question: “Was this document signed by this person?”. As the public key is available to everyone, and can be shared securely, that means that everyone can certify that a document was indeed signed by you. At least, as long as you keep the private key to yourself.
That is quite powerful, and allows us to sign legally binding documents. You sign the document, and send that document along the signature to somebody. Then, this person can use your public key to check your signature.
What’s In A Key?
Keeping your private key secure is key –pun intended– to make this system work. That’s why your private key, contained inside the chip of your ID card, is protected by PIN1 (for authentication) and PIN2 (for signing documents). You need to know them if you want to use the private key.
From a mathematical point of view, both PINs are not really different. They offer access to the private key. The distinction only applies to the type of operation you will perform with them. Ideally, even if they end up in the wrong hands, without the PINs, an evil hacker won’t be able to do much with your private key.
As signing is a very complex and time-consuming process, it would be impractical to sign a whole PDF or Word document. It might take days or even weeks to complete, even with today’s computers. That’s why you don’t usually sign the whole document, but a “hash” of it.

What’s a hash?
A hash is a special summary of the document. It’s another mathematical function that gets a document and returns a small piece of data obtained from it. There are two interesting things about a hash function. First, applying the same function to the same document always gives the same results. Secondly, if you have the hash of a document, it’s impossible to “rebuild” or “recover” the original document. The operation only works in one direction.
As an example, let’s imagine a very simple, homemade hash function. Let’s take the previous paragraph, count the characters, words, vowels and consonants, and put together all that information. The previous paragraph had 448 characters, 75 words, 142 vowels, and 217 consonants. If we concatenate these numbers together, it will give us this hash:
44875142217
No matter how many times we repeat this operation. The results will always be the same when applied to the same paragraph. A different paragraph would, most probably, give us different results. Also, if you ask a friend to build a paragraph with that number, it will be virtually impossible that this person comes up with the right one.
Now, it’s clear that if you want to do a mathematical operation with something, it would be much faster with this small sequence of numbers than with the whole paragraph, right?
Collisions
But what if we find a paragraph that has the exact same characters, words, vowels and consonants? Well, that might happen. That’s why hash algorithms are a lot more complex than this one, and make sure that the probability of a collision (two different texts yielding the same hash) is negligible.
So in reality, when you sign a document, you are not signing the document directly. You are signing a hash of the document. As the same hash of a document should always obtain the same output, signing a hash of a document is virtually the same as signing the document itself, only faster, given that the hash algorithm is good enough.
The Signature Process
Then, signing a document involves this process:
- A hash of the document is generated using a well-known, secure hash algorithm.
- This hash is signed using your private key, asking for your PIN2.
- The hash and the original document are wrapped inside a container, an archive containing both files inside.
These containers, with .asice extension, can be created, opened and verified with the DigiDoc software.

A Digital Signature Is Much More Powerful
Now, the fact that we are signing a hash of the document introduces another powerful aspect of digital signatures. Namely, the ability to guarantee the integrity of the document. Remember our hash algorithm example before? We calculated the hash of our paragraph to be “44875142217”.
Let’s say we sign this hash and send this signature, alongside the original paragraph, to someone. Then, an evil hacker intercepts our message and changes…
“There are two interesting things about a hash function”
for…
“There are two boring things about a hash function”
… before it can reach the recipient, hoping that this person won’t notice the change. However, this altered paragraph has now a different hash, as the letters of the message have changed. While it still has the same words, instead of 448 characters, it has only 443. Vowels and consonants have also changed to 140 and 214 respectively.
That means that the new hash for that document is “44375140214”. Then, if we had signed this hash, we would have obtained a completely different signature.
So when the receipt gets the tainted message and tries to verify the signature, the process will fail. The signature won’t be accepted as valid for that message. Hence, nobody can’t affirm that the modified document has been signed by us.
The Weakest Link
In order for the evil hacker to be able to pass that message as valid, he or she would need to generate a signature for the new hash, and that implies having access to our private key and knowing the right PIN. Thus, as long as our private key remains private, our digital signature offers not only non-repudiation, but integrity validation also.
I know what you are thinking: “What if I find another word or combination of words that have the same letters, vowels and consonants, and thus generates the same hash?”. In that scenario, the signature will be accepted, and the modification of the message will pass undetected.
That’s why the Hash function plays an essential role in this process. Don’t worry though, Hash functions used today are a lot more secure and complex that the toy example I used in this article. They have been designed to avoid collisions to make it impossible to taint a message like we described here.
Ciphering And Deciphering Documents
While less relevant from a legal perspective, ciphering a deciphering documents are also a powerful superpowers granted by your digital identity.
They work like the digital signature, but in reverse. If we sign something with our private key, everyone will be able to verify it using our public key. So what happens if I get a message and apply your public key to it? Well, only you, with the private key, will be able to “undo” this operation.
What use can we get from that? The most obvious one is ciphering a message so only the owner of the private key can decipher it.
That’s precisely how encryption works with your e-Residency card. As your public key is –or should be– readily available to everyone, if someone wants to cipher a message or document so only you can use it, all they need to do is get your public key and encrypt the message with it.

The Key That Protects The Combination Of The Safe
As with signatures, asymmetric encryption is a very time-consuming process. So what usually happens is that a one-time key or passphrase is generated. This is a symmetric key, meaning, it uses simpler algorithms in which both ciphering and deciphering are performed with the same key.
These algorithms are a lot faster, and a big document can be ciphered in a matter of seconds. You cipher it with a key, and use the same key to decipher it.
However, while a lot faster, symmetric cryptography is not considered as secure, as there is only one key, so anyone with access to it will be able to decrypt all your documents. You cannot just share this openly like you would with your public key.
But what happens if we generate one of these symmetric keys, use it to cipher the document, and then cipher the key with the public key of a user?
Then, the key that gives us access to decipher the document will be securely protected. Only the user, who has access to the private key, can decipher the key that we used to cipher the document.
So we get the best of both worlds. We have the speed of symmetric cryptography, and the security of the public-private key pair. It’s like getting the combination to the safe inside a box locked by a key. Anyone with the combination will be able to easily open the safe, but in order to know this combination, you need to have the right key.
Using The DigiDoc Software
Don’t worry if all these concepts seem too complex. Fortunately, the DigiDoc software has a nice, user friendly interface that allows you to sign documents or cipher them.
Signing Documents
The first tab of the DigiDoc application, “Signature“, will allow you to do the former. Just insert your ID card in the USB reader and connect it to your laptop. Open DigiDoc, and drag and drop some documents inside. It will ask you for a name and place to store the container that will keep the documents and the signature together. The container is ready to be signed.
If you inserted the card correctly, the blue button at the bottom right will say “Sign with ID-Card”. If instead it says “Sign using mobile-ID” or something similar, it’s because the software could not read your e-Residency card. Make sure that the reader is properly inserted, the card well positioned, and the light is on, and try again.
To complete the signature, the application will ask you to enter your PIN2 (used to sign documents).
If everything goes well, a green message will appear indicating that the container has been signed, and your name will appear in the list of people who have signed the document, on the right.
You can send this document to other e-Residents, and they can sign it too. They just need to open the container using DigiDoc, and then add their signatures like you did. This is how a document, like a contract or an official resolution, can be signed by all the members of the board of a company, for example.
Ciphering And Deciphering
The second tab of DigiDoc, “Crypto”, will allow you to encrypt or decrypt documents. The public keys of all e-Residents are kept in a database maintained by the Estonian government. The application can access this list.
That’s quite convenient, because it allows us to encrypt a document for one or more recipients, by just knowing their e-Residency ID code. Without the need of downloading or asking for the public key. The application will take care of downloading the right one. You just need to ask this person for his or her personal e-Residency code.
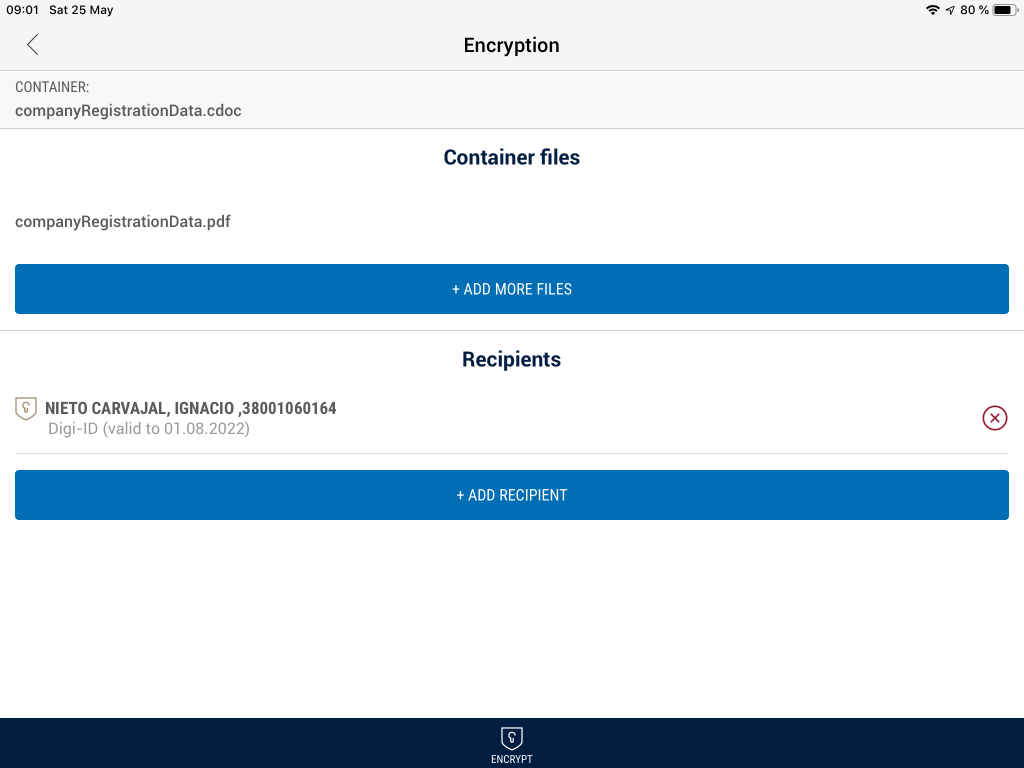
So in order to cipher some documents, just select the Crypto tab and drag and drop these documents inside. Then, you will need to add the recipients, or people who will be able to decipher these documents. DigiDoc makes this very easy.
There is a search field where you can enter the personal e-Residency code of someone. The name of this person will appear, so you can add it to the list of recipients. Repeat this with as many people as you need. Then, click on the blue button to encrypt the documents. This will generate a encrypted container, with .cdoc extension, that you can send to all the recipients.
In fact, you could upload this file in a public folder and share the link on Facebook. While everybody would be able to download the .cdoc file, nobody, except the designated recipients, would be able to make sense out of it.
Deciphering is as easy as opening the .cdoc file using DigiDoc, going to the “Crypto” tab, and clicking on the blue button. Supposing you were added to the list of recipients of the container, you will be able to decipher and extract the contents of the encrypted archive.
Reading Your ID Card Information
The third tab of DigiDoc, “My ID“, gives you information about your e-Residency identity, your certificate, and allows you to change the PINs and the PUK associated to your keys.
Conclusion
So overall, your e-Residency card is a powerful digital identity that allows you to do very interesting things, like digitally signing documents or sending and receiving encrypted documents. The DigiDoc software makes it super easy to access these complex cryptographic operations with just a few clicks.
If you haven’t already, download the application, open it, and play a little bit with it. Try to sign a PDF document and verify your own signature. Or, if you know other e-Residents, ask them for their e-Residency codes, cipher a document, and send it to them, so they –and only they– can open its contents.




Comments ()